CYBER ACON ’22
Social Engineering Awareness
Welcome to our Summit Event page! Discover a world of knowledge, inspiration, and networking opportunities as we bring together industry leaders, innovators, and visionaries at our Summit.
About the event
Tuesday, October 4, 2022 @ 9:00AM - 3:00PM
CYBER ACON ’22
Brocasting Service of Ekiti State.
Social networking sites are websites on the internet that allow users from different regions to connect with each other, share information, images, videos, and to also chat. These websites enable users to make new friends according to common interests. Social networking is the process of connecting through these websites. Recreational clubs and societies are examples of social networking groups. Social networking has evolved from face-to-face networks to online networks with the advent of these websites.
Social networking sites allow users to build online profiles. These profiles are used to connect with friends, friends of friends, and others who have not been in contact for a while. These sites allow uses to create a list of other users with whom they can share information
speakers

Abeleje Oluwatoyin
Protocol Officer(NSCDC)
The role of human error in a successful cyber security breaches and likely solutions

Abigail Inyang
Jr Penetration Tester (MSC Security)
Live demo on SQL injection

Dr. Adebayo Ogundipe
ICT Director(Afe Babalola University)
Detecting, preventing and reacting to human operated ransomwares

Adeosun Joseph
Network Engineer(GTbank)
The role of human error in a successful cyber security breaches and likely solutions

Soji Afinjuomo
IntroTech Officer(FRCN)
The role of human error in a successful cyber security breaches and likely solutions

Olalekan Afuye
The Manger Sterling Bank PLC. Ado Ekiti
Why addressing human error in financial transaction is a top priority?

Akinlawon Fayokun
CyberSecurity Analyst Bochsystems West Africa
Live demo on social engineering and preventing measures

Dr. Olorunyomi Segun
Data Centre Manager (Office of Accountant-General, Ekiti State))
Understanding the increasing problem of digital identity theft through human errors
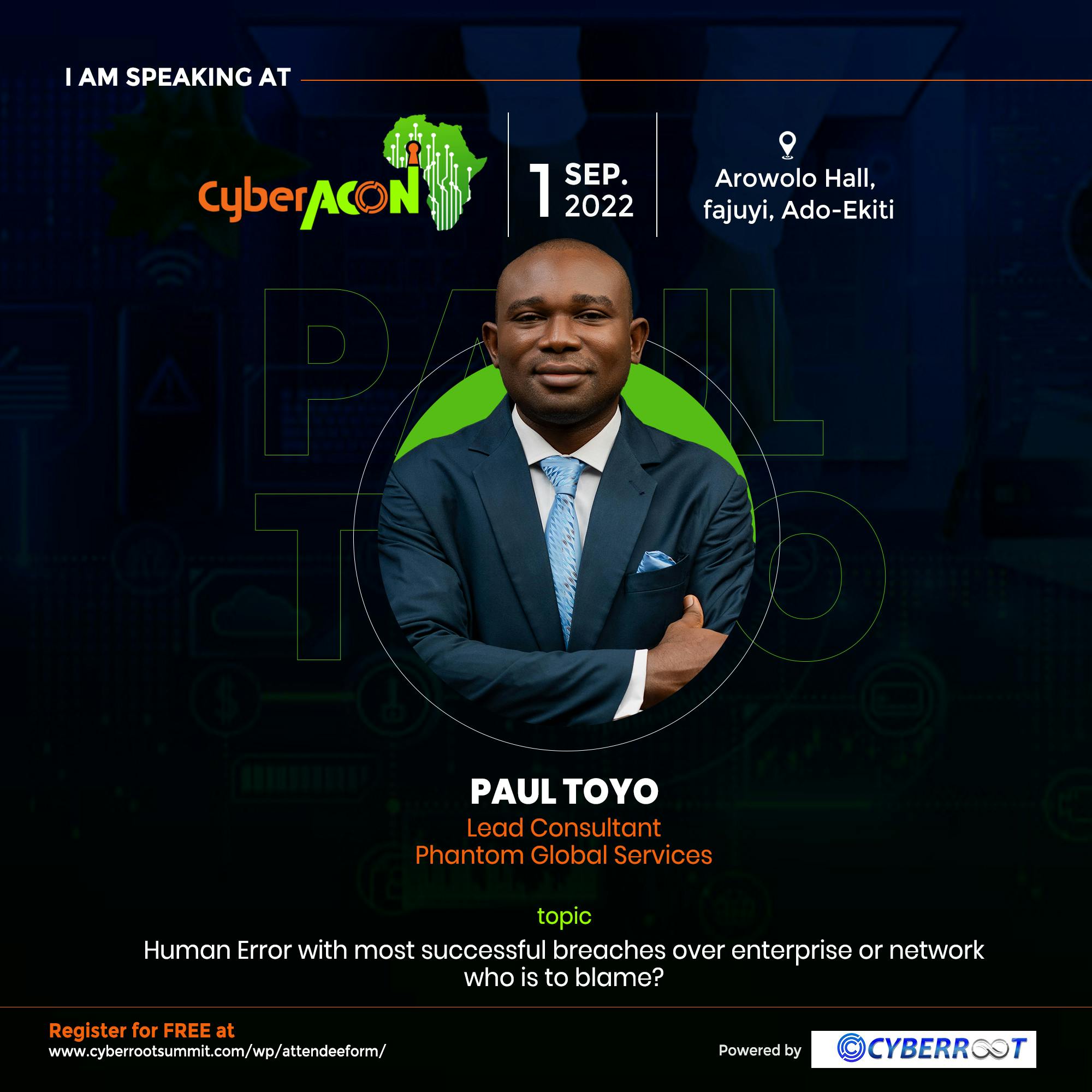
Paul Toyo
Lead Consultant (Phantom Global Services)
Human error with most successful breaches over enterprise or network. Who is to blame?
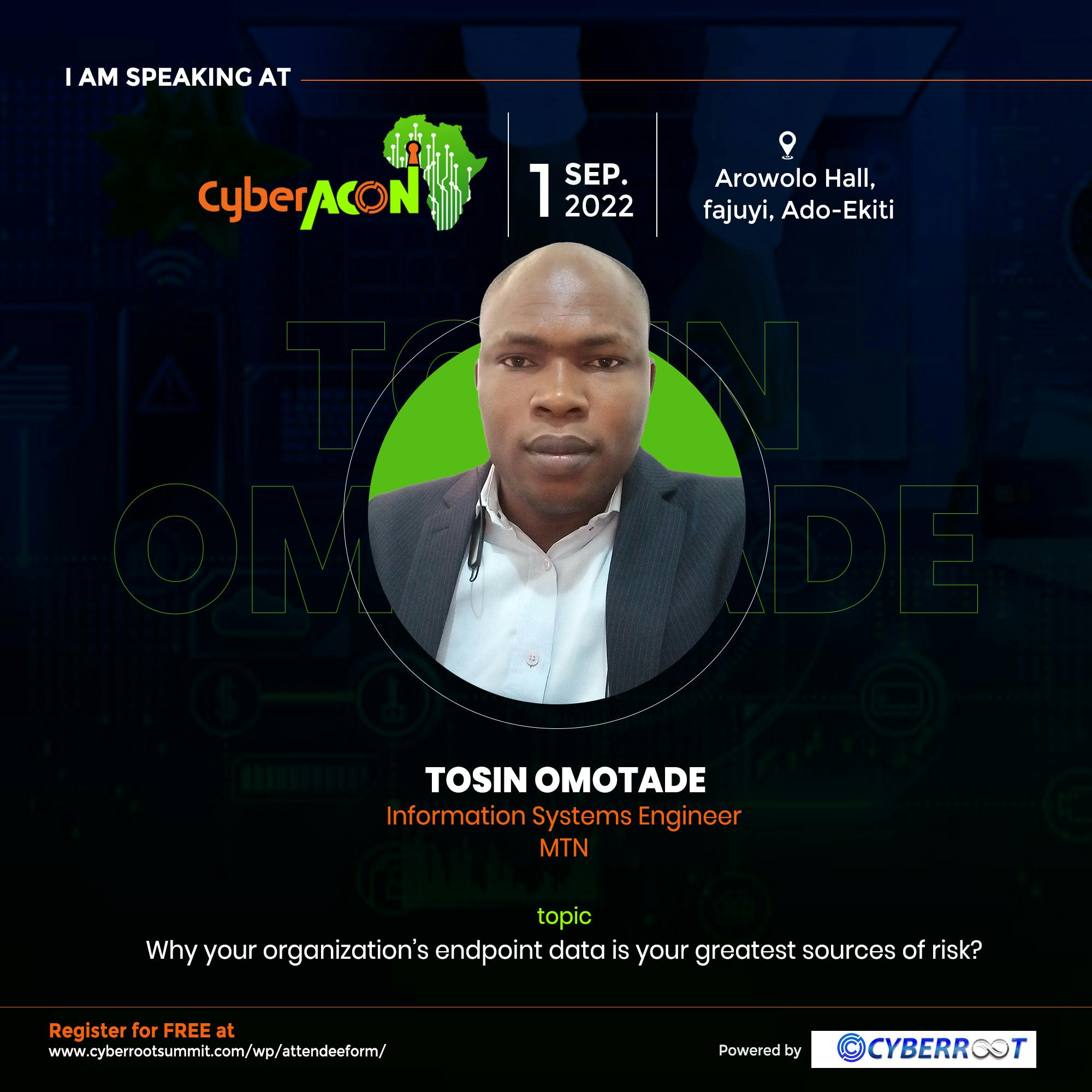
Tosin Omotade
Information Systems Engineer (MTN)
Why your organisation's endpoint data is your greatest sources of risk?

Adaraniwon Oluwatosin
CEO Glimspe Solution Adebayo, Ado-Ekiti
Re-thinking human factor in cyber domain

Sebotimo Victor
Web devloper (Afe Babalola University)
The role of human error in a successful cyber security breaches and likely solutions
Protect your digital assets with our advanced cybersecurity solutions.
Get Expert Advice